Which Factors Make the Blockchain Secure?
Salomon Kisters
Sep 11, 2019This post may contain affiliate links. If you use these links to buy something we may earn a commission. Thanks!
Let’s make it clear right away. The blockchain is secure under certain conditions and cannot be manipulated. But not every blockchain that can be found out there is secure. Fundamentally, the security of a public blockchain is based on a large number of participants and the value of the underlying cryptographic currency.
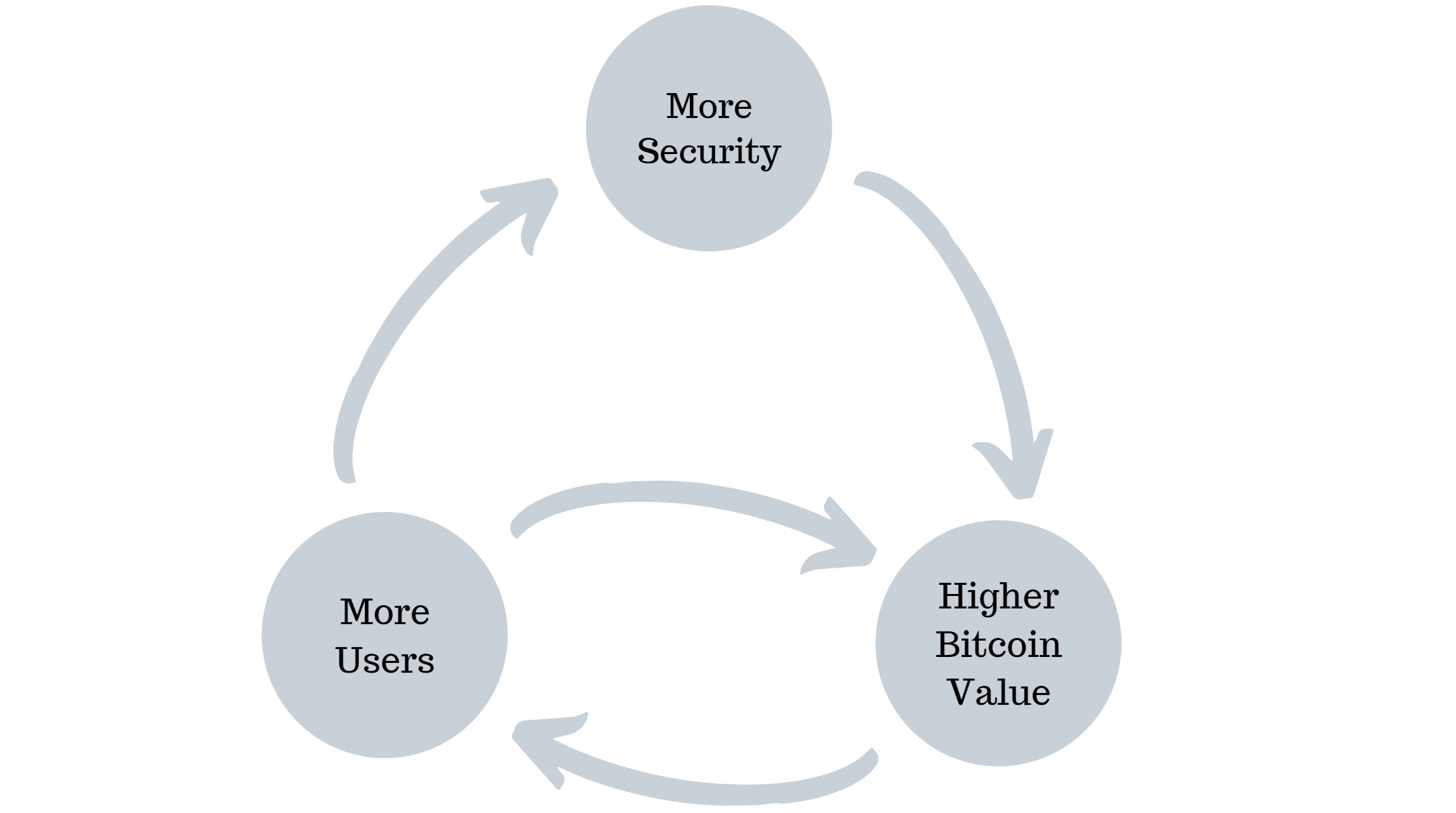
As can be seen in this schematic representation of the Bitcoin ecosystem, more users lead to increased security. And increased security in turn increases the Bitcoin price. All this is ultimately a self-reinforcing cycle in which the users and the value of the underlying currency guarantee the security of the blockchain. This also means that a vulnerability would cause the value of the crypto currency to drop almost instantaneously to zero. This makes Bitcoin’s price a good indicator of the security of the system.
Another way to demonstrate the security of the blockchain is to look at the market capitalization.
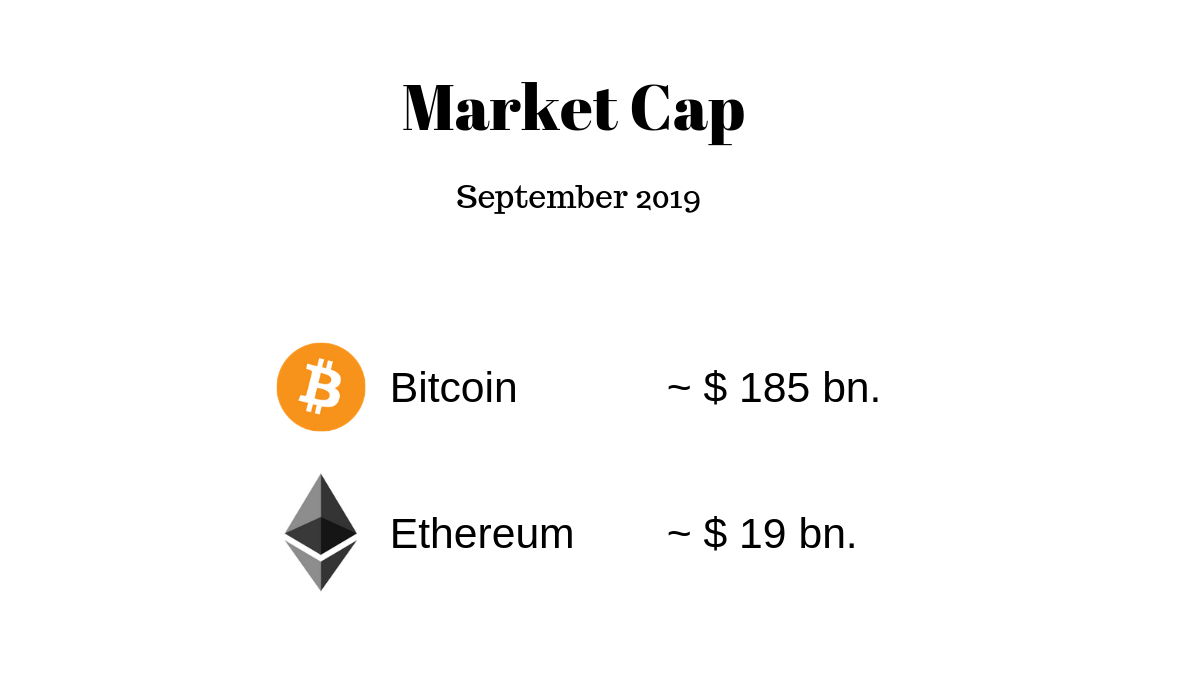
To put it in perspective: Boing has about the same market capitalization as Bitcoin. And this sum is like a permanent bounty that is placed on finding security holes. The fact that despite this bounty in the past few years since the Bitcoin Blockchain existed, no serious safety deficiencies have been detected shows how well thought-out the system is. Based on these considerations, we at OriginStamp also use the two largest and most secure blockchains (Bitcoin and Ethereum) to protect our blockchain-based timestamps.
How more users result in more security
To understand how more users lead to more security, we first need to look at how to reach consensus in the blockchain. If we think about it in detail, it is actually a miracle that a public blockchain works.
A public blockchain is a network in which anyone, including a malicious participant, can participate. Through methods that disguise identity, malicious participants can even participate multiple times. Nevertheless, all benign participants agree after a finite time on a state of the blockchain that was suggested by a benign participant. How is this possible? How does the network know that the new state has been proposed by a benign participant?
A consensus algorithm makes it possible. The best known and most widespread variant is the Proof of Work algorithm. In a nutshell, it works as follows.
- Each participant who wants to propose an new block of data for the blockchain must first solve a cryptographic puzzle.
- Every participant who tries to solve the puzzle is called a miner. The miner mines, so to speak, new blocks for the blockchain.
- The more computing power a participant uses, the higher his chance to solve the puzzle first.
- The person who solves the puzzle first gets the chance to propose a new block of data to extend the blockchain.
- If the proposed extension of the blockchain is accepted as benign by the other participants, the miner who proposed the extension will receive a reward, paid in the respective crypto currency.
As it turns out, a miner has to invest in computing power before he might be able to solve the puzzle and propose a new block of data. Hence the name of the algorithm. The miner must provide a proof of work, i.e. a proof of the computing power used. This artificially created workload is necessary so that there are not too many proposals for a new block in the blockchain. Usually there is just one proposal.
If there are several different valid blockchain extensions, benign participants always behave in such a way that they extend the longest valid blockchain. This ensures that only one state remains valid in the long run. But what possibilities does an attacker have?
What can an attacker do?
There are two basic possibilities that an attacker has. Please note that this section only covers the basics and does not deal with some technical details, such as the mempool.
The first possibility an attacker has is to propose a block that is not valid to the blockchain network. An invalid block can be one for which the cryptographic puzzle has not been solved, or has been solved incorrectly. But it can also be a block where the number of Bitcoins an account owns changes without this being supported by a transaction. All benign participants will ignore an invalid block. Therefore, technically speaking, such an attack cannot be successful. However, the more malicious participants and the fewer benign participants there are, the more likely it is that an attacker will succeed with the second kind of attack.
The second kind of attack is an attack where the attacker proposes a block that is valid, but does not extend the longest valid blockchain. This is particularly relevant for a so-called double-spending attack.
In a double-spending attack, an attacker first spends bitcoins. The corresponding transaction is then documented in the most recent block of the blockchain. In the next step, the attacker tries to make the latest block irrelevant. For this purpose, the attacker extends an older block by several blocks. Thus, the longest valid blockchain no longer contains the block that documents the spending of the Bitcoins. And since benign participants always accept the longest valid blockchain as correct, the attacker gets the opportunity to spend the bitcoins a second time.
However, such an attack can only be successful if the attacker can expand the blockchain with valid blocks faster than would be possible for the benign participants. This is possible in the short term through pure luck. However, to make an older block, where several blocks are already on top, irrelevant, the attacker must be able to mine more blocks in the long run than all other benign participants combined. Technically, this means that the attacker, or a group of attackers, must have the majority of computing power. Therefore, this attack is also called the 51% attack.
The fact that a 51% attack not only doubles Bitcoins for the attacker, but also causes the whole system to collapse is apparent. On the one hand, a systematic 51% attack would immediately be visible for the network. This in turn would cause many participants to leave the network. Much worse, it would lead to mining becoming unprofitable for other miners. Every time a benign miner would have found a new block, the attacker could make that block irrelevant. This would also cause the benign miner to lose his reward and the incentive to continue being a miner of the blockchain.
But even if an attacker could combine 51% of the computing power, it would be almost impossible for him to manipulate data within older blocks, e.g. timestamps created with OriginStamp.
Why can’t old data be manipulated?
To understand why old blocks in a blockchain cannot simply be manipulated or deleted, we need to take a look at the blockchain data structure. And in order to understand how the data structure works, we need a basic understanding of hashing.
So what’s a cryptographic hash? A cryptographic hash (more precisely a hash value) of a data set is calculated using a cryptographic hash function. An example of a cryptographic hashing function, which we also use at OriginStamp, is the SHA-256 hashing function. It has some important properties.
- A digital document of any length is accepted as input.
- The output is a string of fixed length.
- It is a mathematical one-way function. This means that the original document cannot be recalculated from the hash value.
- It is practically impossible to find two datasets that have the same hash value.
- If a random hash value is specified, it is infeasible to create a dataset that maps to the hash value.
- If the original data set changes even slightly, it maps to a completely new, unpredictable hash value.
Put simply, a hash value represents a data set in the same way as a fingerprint represents a person. And as fingerprintes, cryptographic hashes are ubiquitous. Areas of application include password storage, credit card transactions, or secure surfing on the Internet. Therefore there are a lot of calculators and libraries to calculate a hash quickly and without much effort. In a programming language, creating a hash from a data set usually requires only one line of code. But there are also various websites, with which a hash of a file can be calculated with just one click.
Let’s take a look at the blockchain data structure.
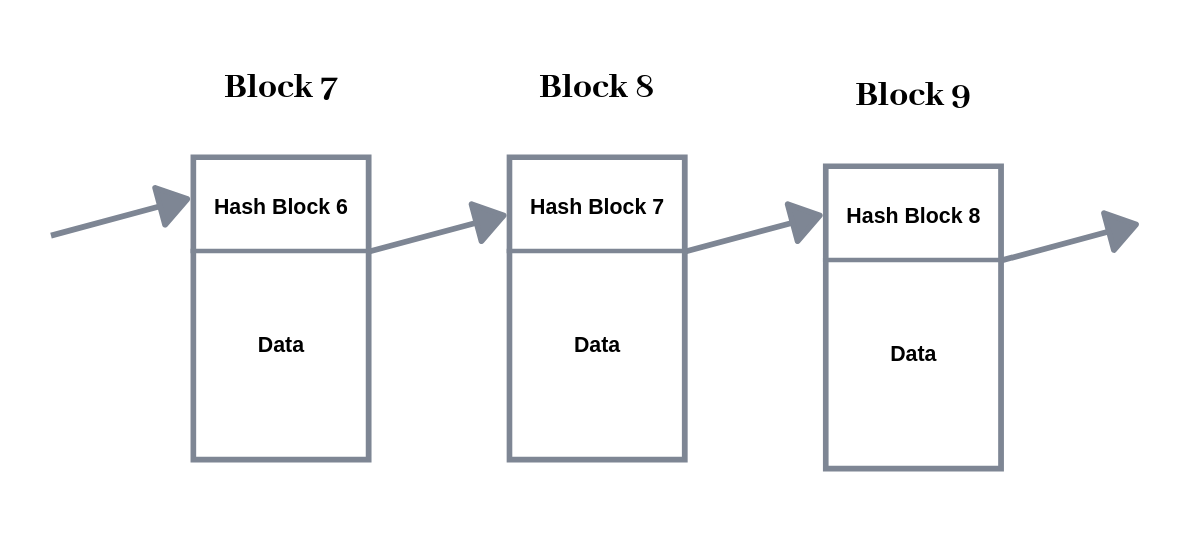
We can see that the blocks are linked to each other. More precisely, each block contains the hash value of the previous block. Now, what would happen if someone were to manipulate the data in Block 7? First, the hash value of block 7 would change. However, since the hash value of block 7 is also contained in block 8, the hash value of block 8 would also change. This means that the blockchain after a manipulation is either shorter, or invalid, or all subsequent blocks would have to be recalculated.
Since the benign participants of a blockchain network always only accept and extend the longest valid blockchain, an attacker would not only have to manipulate one block, but would have to recalculate all blocks created after the manipulated block. But as long as the attacker does not have more than 50% of the total computing power, the manipulation-free blockchain will always grow faster than the manipulated version on average. This makes a public blockchain with many users so secure.
Further enhancing this security, technologies like threshold signatures are being developed. These advanced methods provide additional layers of protection and efficiency, demonstrating the evolving landscape of blockchain technology and its continuous efforts to strengthen security measures.
Who has the power?
In the discussion about the security of the blockchain an important question arises. Who determines the rules? Who, for example, determines the criteria by which it is measured whether a block in the blockchain is valid?
Let’s take a look at Bitcoin. It turns out that the developers working on the reference implementation of the Bitcoin software set the rules. The rules of the reference implementation are adopted by all benign participants of the Bitcoin network. In most cases the reference implementation is used directly. In contrast, Ethereum does not have a reference implementation but a yellow paper documenting the rules. In both cases, there is a small group of people who determine the rules. Why isn’t this a problem?
It does not pose a problem, as the rulemakers are observed by the miners. And miners will only operate a blockchain with whose rules they agree. And a blockchain without miner is useless. Does this mean that the miners have all the power?
The miners also don’t have all the power, because they must choose the blockchain where they can profitably mine new blocks. This is directly related to the price of the crypto currency. The price today is mainly driven by speculation. Therefore, investors have a big influence on which blockchain miners are operating at.
And investors speculate on the further spread of the underlying crypto currency, therefore on more users who use e.g. Bitcoin for payment. So all users of a blockchain have an influence on the investors and thus also indirectly an influence on the rules.
Finally, one could argue that users don’t care about the underlying crypto currency. A user doesn’t care if he finally pays with Bitcoin or Ethereum. Therefore, also services that make crypto currencies usable for everyone have a big influence.
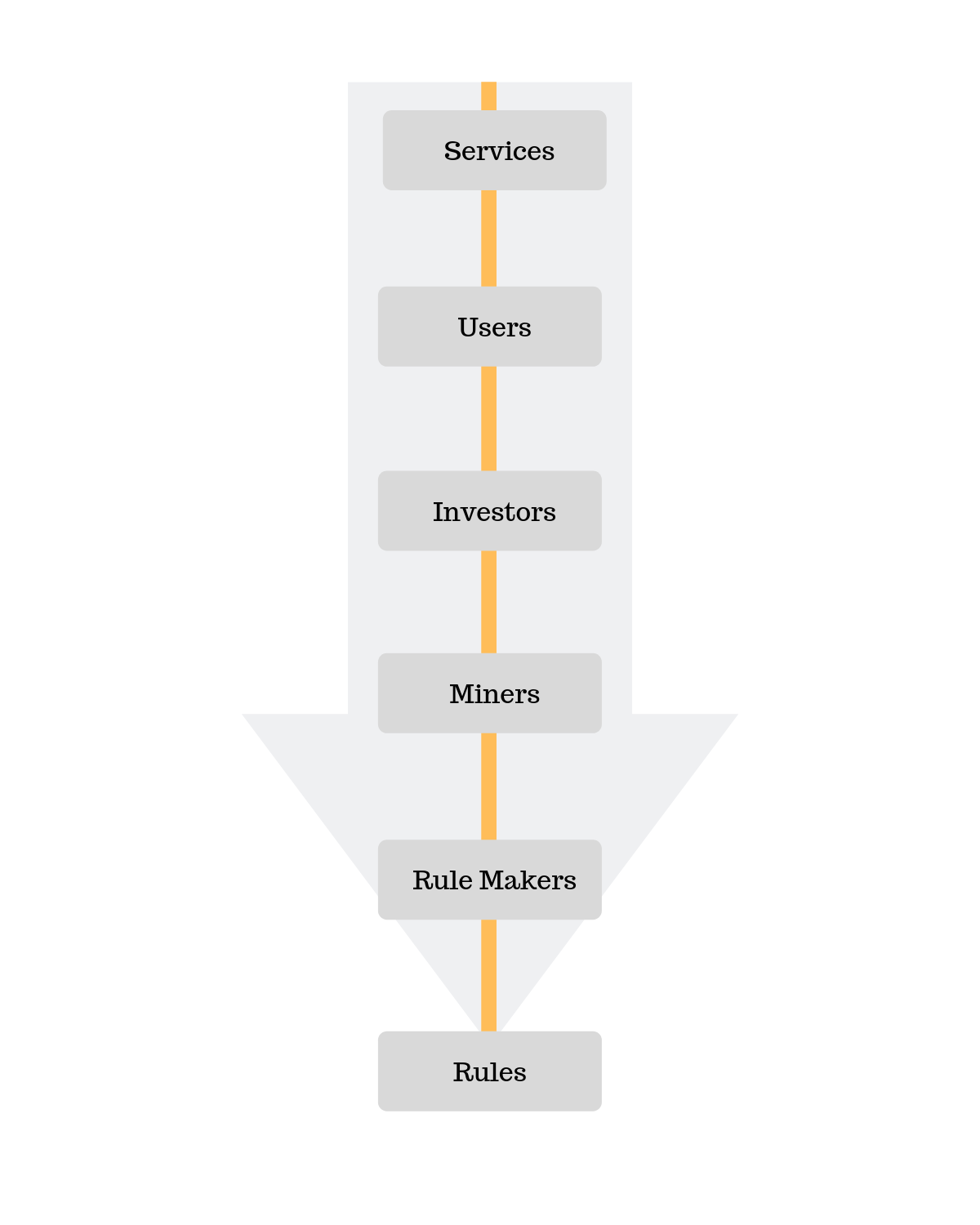
It becomes evident that the power is well distributed in a carefully designed, public blockchain. This makes the blockchain attractive and revolutionary. There are no individuals or groups that unite all power.
What are the implications for blockchain-based timestamping?
First of all, we can summarize that the blockchain is an extremely clever construct, which can act as a tamper-proof data storage. And the more participants a blockchain has, the more difficult it becomes to manipulate data in the blockchain. Therefore, as far as we know today, most large public blockchains, including both the Bitcoin and the Ethereum blockchain, are extremely hard to manipulate.
The main purpose of the blockchain-based timestamp method used by OriginStamp is to automatically create a large number of witnesses for data sets who can testify that a data set already existed at a certain point in time. The blockchain is optimal for this purpose, because a hash of a data set can easily be embedded in a block of a public blockchain.
Say the Bitcoin blockchain could be manipulated unexpectedly. What would happen in the worst case if the blockchain were manipulated and the Bitcoin value dropped to almost zero?
First, we use several blockchains in parallel for OriginStamp. Bitcoin, Ethereum and AION. In addition, we secure the timestamps made in a daily newspaper, the SÜDKURIER, with over 360,000 readers.
And secondly, manipulating the blockchain does not necessarily mean that old data entries would be overwritten automatically for all participants of the manipulated blockchain. Therefore it would be very likely that enough witnesses for old timestamps would still be preserved to have sufficient evidentiary value.
In conclusion, it can be said that large, highly decentralized, public blockchains are damn secure. And that the blockchain-based timestamps made with OriginStamp are even more secure.
Stay informed with the latest insights in Crypto, Blockchain, and Cyber-Security! Subscribe to our newsletter now to receive exclusive updates, expert analyses, and current developments directly to your inbox. Don't miss the opportunity to expand your knowledge and stay up-to-date.
Love what you're reading? Subscribe for top stories in Crypto, Blockchain, and Cyber-Security. Stay informed with exclusive updates.
Please note that the Content may have been generated with the Help of AI. The editorial content of OriginStamp AG does not constitute a recommendation for investment or purchase advice. In principle, an investment can also lead to a total loss. Therefore, please seek advice before making an investment decision.

Top Blockchain Startups to Watch in 2021 - Innovative Use of Blockchain Technology
Discover the top blockchain startups of 2021 that are innovatively using blockchain technology to reshape various industries.

Using Blockchain Technology to Differentiate Your Business - A Competitive Advantage Guide
Learn how to leverage blockchain technology to gain a competitive advantage in your business. Explore examples and benefits of using blockchain for non-functional requirements.

Benefits of Blockchain in Fintech: Trust, Cost Savings, and Transparency
Discover the benefits of blockchain in fintech, including trust, cost savings, and transparency. Learn how blockchain can revolutionize the industry.
Protect your documents
Your gateway to unforgeable data. Imprint the authenticity of your information with our blockchain timestamp